Over the past decade, people have increasingly been drawn to remote work. In fact, remote work grew by 159% between 2015 and 2017.
When COVID-19 slammed the world in 2020, the acceleration towards remote work hit a new gear. Suddenly, many business owners were forced to enable their employees to work from home. It was the only way to survive!
Most business owners have found the shift to remote work positive but challenging.
When employees work from home offices, there are some distinct advantages. For instance, you don’t have to spend as much money on real estate. However, you need to make sure your employees are equipped, efficient, and safe from cyber attacks.
At Straight Edge Technology, we understand the helpless feeling of worrying about cybersecurity. It’s an awful place to be, and we want to help.
That’s why we’ve written this article on how you can keep your employees that are working from home safe (and, in doing so, protect your business!)
Ready to start learning? Let’s get you back to feeling safe and secure about your company.
*Feel free to read through the whole article, or simply click a section in the Table of Contents to go directly to that topic*
Why Remote Work Isn't Going Away
All the indicators seem to be pointing in one direction:
The recent move towards remote work is here to stay.
Why?
Because the benefits of working from home seem endless, both for employees and employers. Here are just a few examples:
1 - Remote Workers Are Happier
Remote workers report a Workforce Happiness Index of 75 out of 100, compared to 71 for in-office employees. And, remote employees are more likely to report being satisfied with their jobs than office-based workers (57% vs. 50%).

A good team leader knows that happy employees stick around longer. And when you can retain long-term employees, your company has more total experience, which increases efficiency and productivity.
I mean, who wouldn’t want to attract and retain good talent?
2 - Employees Are Willing To Sacrifice To Work From Home
7% of workers say that the ability to work from home is so important that they are willing to take a 10% to 20% pay cut to work remotely.
We don’t actually encourage cutting pay for remote workers, but simply mention this to prove how many people want to work from home.
And while reducing pay may not be an ethical way of cutting overhead costs, the money you can save on rent, utilities, coffee and office supplies, and more is significant!
Of course, when you cut overhead costs, you make your business more profitable.
3 - Remote Work Leads To Improved Mental Health
Believe it or not, remote work can support mental health.
Why?
Because flexible work options create better mental health. In fact, employees without access to flexible work are nearly two times more likely to have poor or very poor mental health.

These are just three reasons why over 80% of company leaders plan to permit remote work after the pandemic and why an Upwork study predicts that 22% of the American workforce will be remote by 2025.
Here’s the bottom line:
Remote work from home is here to stay. As a business owner, you will likely have employees working from home, at least part-time in the future.
You need to start planning and preparing now, so you can protect your business from the myriad of cyber attacks that are sure to come as scammers seize this new opportunity.
For more information, read our blog: Implementing A Remote Workforce Plan For Your Business.
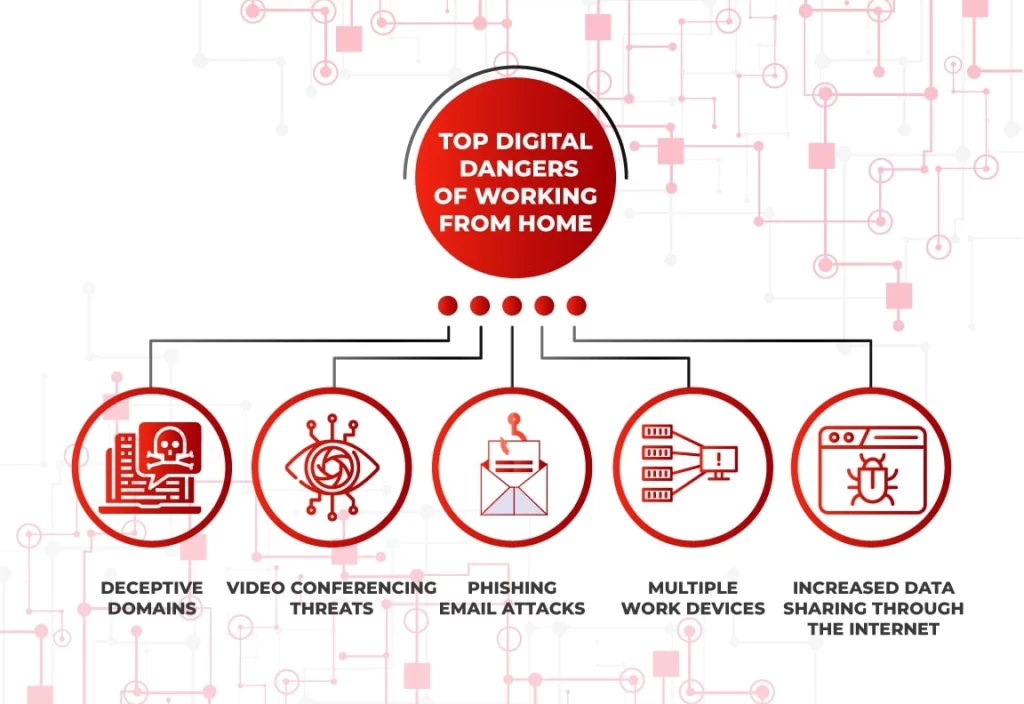
The Dangers Of Working From Home
Digital security breaches increased in 2020 because hackers correctly guessed that many people would spend more time on their devices—both for leisure and work.
Hackers have particularly focused on the new “opportunities” that increased remote work has presented to them.
For example, Barracuda Networks reports that phishing email attacks increased more than 600% in the early days of the Covid-19 crisis.
But before we get into practical actions you should take to secure your business, we need to understand the threats you’ll be facing.
Here are the main things you should monitor closely in your remote workforce.

Legitimate Looking Domains That Are Malicious
When clicking onto a website that might be sketchy, we tend to look at the domain name first to see if it looks legitimate.
For example, we would trust domain names like “wikipedia.org” or “espn.com.”
However, since the spike in remote work, hackers and scammers have created domain names that appear legitimate but are not—especially concerning software used regularly by remote workers like Zoom and Google Classrooms.
In fact, more than 1,700 new domains related to Zoom were registered in the first several months of 2020.
Beyond that, researchers were able to detect malicious files containing the word “Zoom,” such as “zoom-us-zoom_##########.exe” (# representing various digits).
Running these files would install “InstallCore PUA” on the user’s computer, allowing other users to install malware.
Scary, right?
(You can learn more by reading our blog: Top 7 Cybersecurity Threats For Businesses In 2021 (And How To Prevent Them).
Video Conferencing Threats

For example:
In early 2020, a vulnerability in Webex allowed unauthenticated users to join private meetings with just the meeting ID and a mobile Webex app.
Another example of a video conferencing threat is Zoom bombing, or strangers crashing private video conference calls to perform disruptive acts. Companies and schools holding online classes have fallen victim to this.
While this might seem like a minor annoyance, it could become a significant issue when discussing highly confidential or sensitive information.
In addition, hackers can also use the chat portion of these tools to spread malicious links or upload files.
Phishing Email Attacks

In its most basic form, phishing occurs when a hacker uses a false identity to trick someone into providing sensitive information, downloading malware, or visiting a site containing malware.
The thing about phishing is that it’s not just business emails that are vulnerable.
Since personal email accounts are often housed on the same laptop used for business, hackers can use them to compromise the whole system.
In other words:
You may secure your employee’s business email accounts, but if you’ve provided them with a laptop to work from home, and they sign into their unprotected personal email account, hackers could gain access to the entire system.
Employees Using Multiple Devices To Work
Employees frequently use more than one device when working from home to access important information or other work-related things.
This complicates the implemented efforts for protecting data as every device used is a potential entry for system threats.
For instance, the employee’s laptop may have sufficient security controls, but using an insecure smartphone may enable cybercriminals to compromise the organization’s data.
Increased Data Sharing Through The Internet
In an office environment, employees generally use secured communication infrastructure and intranets (a local or restricted communications network) to communicate and exchange information.
On the other hand, work-from-home interactions are increasingly dependent on home security systems that rely on the internet service provider’s router.
This is a huge risk since public Internet connections are insecure and often full of malicious actors.
The connection used may contain several flaws that a cybercriminal can compromise, intercepting every piece of data transmitted through the wide-area network.
How To Combat The Risks Of Remote Work
All these threats can seem overwhelming.
And truthfully, any organization that does not have proper cybersecurity training and software in place will eventually fall victim to a cyberattack.
Let’s dig into what you can do to keep your remote workforce safe and protect your business.
To start, we’ll discuss video conferencing and what you can do to keep your digital communications safe.
Tips For Protecting Your Video Conferencing
If you want to deter “Zoom bombing” and other video conferencing threats, here are a few steps you can take:
- Ensure that meetings are password protected: This protects your session even if an external user somehow accesses your meeting ID.
- Don’t share meeting information on public platforms: Although it may seem convenient to share meeting info on public platforms, doing so can lead to disruptions and other malicious activity.
- Use host controls: Most video conferencing tools offer host controls that allow you to moderate a meeting or disable chat features. You can use them to remove participants or lock the meeting altogether.
- Utilize waiting rooms or lobbies: Of course, these aren’t physical spaces. But most video conferencing tools allow you to enable waiting rooms – which means you must grant any user access to that particular meeting.
- Disable file transfer features: Like we already mentioned, hackers can use meeting rooms to upload malicious files – and sometimes those files are downloaded by participants.
And remember: these tips aren’t just for business owners. Make sure you inform your remote workers about proper video conferencing protocol and encourage them to follow the same rules.

Now, let’s explore some other practices that can keep devices and information protected, even with a remote workforce.
Invest In Comprehensive Antivirus Software
Installing a sound antivirus system on all devices should be a requirement for your employees.
And honestly, it’s worth your money as an employer to pay for the software. After all, antivirus suites take on the hard work of offering automatic remote working security against a host of threats, including:
Not only can a comprehensive antivirus suite fend off online security threats, but it also automatically updates itself to stay on top of new and emerging threats.
If you’re looking for some antivirus suggestions, we recommend Norton, TotalAV, and Bitdefender.
Set Up Two-Factor Authentication
We get it—two-factor authentication can be unhandy.
If you’re unfamiliar with two-factor authentication, it is when a passcode is sent to your phone or email address when you log in to ensure a hacker isn’t using your account.

But trusting passwords only has been a historically bad idea.
For example, back in 1961, the Massachusetts Institute of Technology developed the Compatible Time-Sharing System (CTSS).
To ensure everyone had an equal chance to use the computer, MIT required all students to log in with a secure password. Students soon figured out that they could hack the system, print out the passwords, and hog more computer time.
Trust us on this one: passwords have time and again been hacked, leaked, or stolen.
If you want to secure your business data, you need to make sure everything is controlled with two-factor authentication.
Give Employees A Work Computer
Giving your employees a work computer allows you or an IT professional to set up proper security measures on the computer.

You can also require that all company work is done on that computer, which decreases the number of vulnerable gateways for hackers to access your system.
Just remember:
You might need to remind your employees that their family members should stay away from work devices.
While you can train your employees in proper digital safety protocol, you can’t train all their friends and family! And when computers are at home, they are exposed to children and other people.
Thankfully, when you provide a work computer to your employees, you have some authority in determining what they should or should not do on that computer.
Make Sure Your Company VPN Is Strong
When employees work on-premises, they can connect their computer and mobile device directly to the business’s internal network.
However, if an employee works remotely, their connection to that internal network must occur over the public Internet, potentially exposing their traffic to cybercriminals.
That’s where a VPN (virtual private network) comes in.
A VPN creates an encrypted connection between user devices and one or more servers.
In other words:
VPNs can securely connect a user to a company’s internal network.
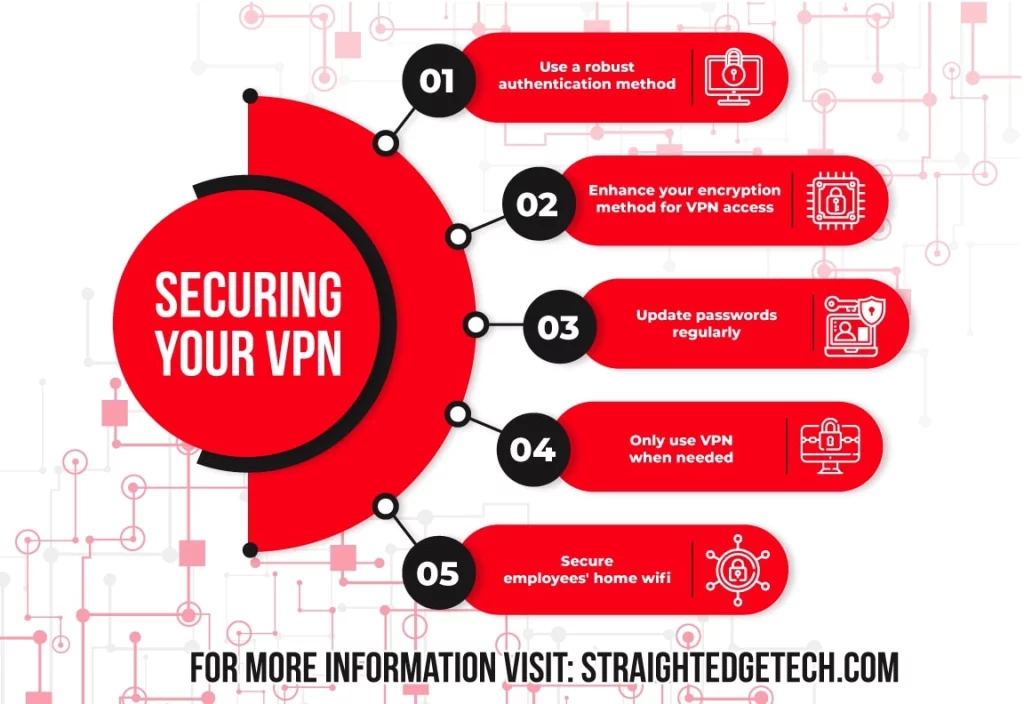
However, not all VPNs are created equally. Here are a few ideas to make sure your VPN is strong and secure:
- Using the most robust possible authentication method—many VPNs simply use a username and password, but you may want to think about upgrading to the use of smart cards.
- Enhance your encryption method for VPN access—for instance, if you are only using a Point-to-Point Tunneling Protocol, you may want to upgrade to a Layer Two Tunneling Protocol (L2TP).
- Ensure employees are updating their passwords regularly—it doesn’t matter how strong your VPN is; if an employee’s password is compromised, it will give hackers an easy way in.
- Make sure employees are only using the VPN when they need it—if your employees are using their work laptops for personal jobs in the evenings and weekends, remind them to switch off the VPN.
- Ask employees to secure their home wifi—while working from home, employees will be using their home networks and internet connections. Unfortunately, these could also be compromised.
Train Employees In Securing Home Wireless Networks
Like we just mentioned, the home networks and internet connections that employees use could be compromised.
Therefore, train your employees to take the following security measures on their home networks:
- Create a strong, unique password—you can do this by going to your router settings page (type “192.168.1.1” in your browser) and entering your current username and password, then changing the password under settings. Choose a password that would be difficult for anyone to guess – ideally, it should include a mix of lower-case and upper-case letters, numbers, and punctuation.
- Change your SSID—this is the name of your wireless network. This, once again, can be changed on your router settings page. Try to make it something cryptic and challenging to guess. Do not use your name, home address, or anything that could be used to identify you.
- Enable Network Encryption—this can usually be done under security settings on your wireless configuration page. You will have several security methods to choose from, such as WEP, WPA, and WPA2. The strongest is WPA2.
Use A Password Manager
Regularly updating passwords and making sure those passwords are strong is an essential step to securing your business data.
The problem is that humans can’t remember multiple passwords that are a mix of numbers, symbols, and characters.
Thankfully, there are password managers that can do the work for you.

Software like LastPass can generate strong passwords and then remember them for you, so logging in is quick, easy, and secure.
Hire A Cybersecurity Expert
Hiring an IT professional is a great place to start.
They should be able to help you with services like network security and web filtering and firewall.
Just make sure you choose a company that offers 24/7 service. Digital security breaches aren’t the kind of thing to play around with – and when one occurs, you need to get help immediately.
How Straight Edge Technology Can Help
The world is riding on the back of digital connection. As a business owner, you should work towards finding business security, even with a growing remote workforce.
If you are looking for someone to help you keep your business data safe, contact us at Straight Edge Technology.
We can help you secure your network. We also offer Managed IT services and Cloud IT solutions so you can focus on growing your business.
Contact us to see how we can help your business. We look forward to hearing from you!
Read our recent blog posts on different IT services, challenges, and tips!

7 Ways Law Firms Can Benefit From 24/7 IT Monitoring
In the fast-paced world of law, where every second counts and sensitive client data must be protected at all costs, technology plays a pivotal role

Lunch and Learn: Hurricane Preparedness Form & Checklist
Straight Edge Technology recently hosted a Lunch and Learn where we explored crucial topics related to Hurricane Preparedness and Disaster Recovery. In our ongoing effort

Managed IT Services: A Key Partner In Healthcare Disaster Recovery Plans
In today’s digital landscape, healthcare organizations face a unique set of challenges in maintaining the security and accessibility of their data. From patient records to

