As you plan your well-deserved vacation, ensuring the security of your home is likely at the top of your checklist.
Locking doors, concealing valuables, and perhaps even setting up a security system are all measures we take instinctively to protect our physical assets.
But in today’s increasingly digital world, safeguarding your business data is just as critical – if not more so – as protecting your home.
At Straight Edge Technology, we understand the paramount importance of fortifying your business against the ever-evolving landscape of cyber threats.
In this post, we delve into the fundamental concept of network firewalls – your first line of defense against cyberattacks – and explore their vital role in maintaining the integrity and security of your business data.
SO, WHAT EXACTLY IS A NETWORK FIREWALL?
In essence, a firewall acts as a barrier between your private network and the vast expanse of the public internet.
Much like a sturdy lock on your front door, a firewall serves to prevent unauthorized access to your network infrastructure, thereby thwarting potential cybercriminals from infiltrating your systems, stealing sensitive data, or launching malicious attacks.
Learn more about the Top 5 Cybersecurity Threats for business owners this year.

WHY IS IT CALLED A “FIREWALL”?
Your private network allows you to share data between computers and access shared printers, scanners, and copiers at your business.
However, the flip side is that if a hacker gets access to the network, they can steal an enormous amount of data, plant malware, or commit some other kind of cyberattack.
The purpose of a firewall is to protect your private network from the public internet so that cybercriminals won’t be able to break in and commit these attacks.
BUT HOW DOES IT WORK?
Think of a firewall as a vigilant gatekeeper stationed at the entrance to your digital domain.
It meticulously inspects all incoming and outgoing data packets, allowing legitimate traffic to pass through while blocking or flagging any suspicious activity based on predefined criteria such as IP addresses, domain names, protocols, or keywords.
By effectively filtering and regulating the flow of data, a firewall serves as a crucial line of defense against cyber threats, helping to safeguard your business assets and preserve the confidentiality, integrity, and availability of your information.
Network Firewall Vs. Host-Based Firewall
Many computers have a firewall built into their system as part of the software. For example, your antivirus software also has a built-in firewall. These are host-based firewalls because they protect a singular computer.
On the other hand, a network firewall protects an entire private network. That’s why they’re popular with businesses, especially a business handling sensitive data.
But remember, any business can have its data stolen by cybercriminals! Cybercriminals often go after smaller businesses because they assume their data won’t be as rigorously protected.
No matter the size of your business, you should look into getting a network firewall.
But what type of network firewall is right for you?
Five Types Of Network Firewalls (And How To Choose The Right One)
There are multiple types of network firewalls on the market. This is great for you because it means there’s an option out there that meets your needs.
But it can also be frustrating to know which kind to choose!
Let’s go over five types of network firewalls, what they each do, and how you can know if it’s the right type for you.
1. Packet Filtering Firewalls
These foundational firewalls operate at the network layer and make decisions based on information contained in the packet headers, such as source and destination IP addresses.
While relatively basic in functionality, packet filtering firewalls offer a cost-effective solution for smaller organizations or as part of a layered defense strategy.
2. Circuit-Level Gateways
These foundational firewalls operate at the network layer and make decisions based on information contained in the packet headers, such as source and destination IP addresses.
While relatively basic in functionality, packet filtering firewalls offer a cost-effective solution for smaller organizations or as part of a layered defense strategy
3. Stateful Inspection Firewalls
Unlike their stateless counterparts, stateful inspection firewalls maintain awareness of the state of active network connections, allowing them to make more informed decisions regarding the passage of traffic.
By analyzing both packet headers and contents, these firewalls offer enhanced security and threat detection capabilities, albeit at the potential cost of increased processing overhead.
4. Application Or Proxy Firewalls
Positioned at the application layer of the OSI model, application firewalls offer deep packet inspection and granular control over application-layer protocols and traffic.
By acting as intermediaries between clients and servers, these firewalls provide an additional layer of security by scrutinizing and filtering application-specific data, thereby mitigating the risk of protocol-based attacks and application-layer vulnerabilities.

5. Next-Generation Firewalls
Representing the pinnacle of firewall technology, next-generation firewalls combine traditional firewall functionality with advanced security features such as intrusion prevention, application control, and deep packet inspection.
By employing sophisticated threat detection algorithms and behavioral analysis techniques, these cutting-edge firewalls offer unparalleled protection against a wide range of cyber threats, making them the preferred choice for organizations with stringent security requirements and complex network environments.

WHAT HAPPENS IF YOU DON'T HAVE A FIREWALL
What does that mean?
It’s like leaving the front door of your business open when you go home for the night. You might be fine, but you’re just inviting someone to come in and wreak havoc.
Cybercriminals target businesses with no firewall and execute malicious code remotely. They spread malware such as viruses or ransomware, costing small businesses an average of $10,000 to get everything fixed.
Not only that, but by giving criminals access to your entire network, they can infect interconnected devices.
Every business should have a firewall. But the bigger you are, the more sensitive your data is, and the more computers you have on your network, the more critical it is to ensure your firewall offers top-notch protection.
OTHER PROTECTIVE MEASURES YOU CAN TAKE
It’s always a good idea to have a layered defense system instead of relying on just one thing to keep your data secure.
For instance, when you park your car on the street, you probably lock your doors. You probably also shove valuable items out of sight.
On top of that, you might take your most valuable items with you.
By taking multiple protective measures, there’s a higher chance that your items will be safe.
In the same way, don’t rely on firewalls alone to keep your data safe and your Internet secure.
So what other protective measures can you take?
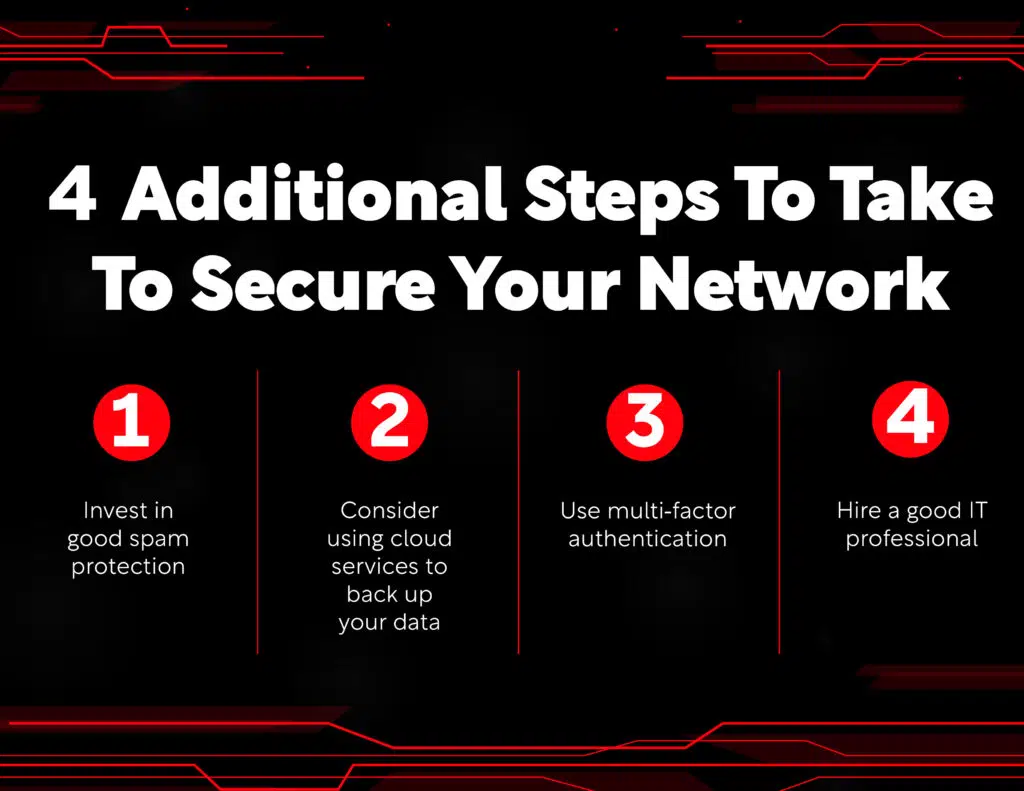
Make sure you have good spam protection to keep malware from entering the network through a spam email link.
Consider using cloud services to back up your data.
Use multi-factor authentication to keep your accounts from being compromised by cybercriminals.
And finally, make sure you hire a good IT professional who can help you with disaster recovery if anything should go wrong!
CONCLUSION
At Straight Edge Technology, we’re dedicated to empowering small businesses like yours with the tools, expertise, and support needed to navigate the complexities of modern cybersecurity threats successfully.
Our mission is to provide proactive, tailored solutions that not only mitigate risks but also foster resilience and enable sustainable growth.
Ready to take the next step towards safeguarding your business’s digital assets?
Contact us today to speak with one of our cybersecurity experts and discover how Straight Edge Technology can help you fortify your defenses, protect your data, and achieve peace of mind in an increasingly interconnected world.

