Our world lives, works, and plays on the internet.
And while the internet increases our connectivity and efficiency, it also brings numerous threats, such as cyber hacking and online attacks.
More than ever, we feel a need for cybersecurity.
According to Norton Security, nearly 60 million Americans have been affected by identity theft. In 2023, it is estimated cybercriminals will be stealing 33 billion records per year.
These cyberattacks target everyone, but trends show small businesses are one of the most common targets. In fact, approximately 43% of cyberattacks target small businesses!
Thankfully, there are software and online security measures available to help protect your business from cybercriminals.
We've Put All This Information Together Into A Guide So You Can Save For Later!

To help your business be prepared and secure for the coming year, Straight Edge Technology has identified 8 of the top cybersecurity threats for 2022 and what your team can do to prevent them.
We’ll also look at a brief history of cybersecurity and the four most common online attacks.
Keep reading to equip your business with proper cybersecurity for 2022 and beyond!
*Feel free to read through the whole article, or simply click a section in the Table of Contents to go directly to that topic*
Table Of Contents
8 Cyber Security Threats In 2022 & Their Solutions
A Brief History Of Cybersecurity
Before we jump into the common online threats and attacks, let’s briefly look at what cybersecurity is and how it has evolved during the technology era.
What Is Cybersecurity?
Cybersecurity is a bit of a buzzword, and people have different definitions in mind when discussing it.
According to Wikipedia, in its most basic form, cybersecurity is “the protection of computer systems from the theft of or damage to their hardware, software, or electronic data, as well as from the disruption or misdirection of the services they provide.”
While this definition is a mouthful, it highlights two aspects of cybersecurity not often considered.
First, very few people think of the hardware or physical computer components when they think of cybersecurity.
Why not?
Because in today’s world, cybersecurity is usually associated with internet and software attacks and not physical computer hardware.
Second, cybersecurity was a threat before the internet.
Since the first computers started storing data, thieves have been trying to steal it! And while this was more difficult before the internet, it did occur.
First Cyberattacks
When did the first cyberattack occur?
Believe it or not, one of the first cyberattacks was more of a game than an attack!
In 1971, Bob Thomas developed a computer program able to travel between connected computers.
Unlike most of today’s attacks, his program did no damage. Instead, it simply displayed a message stating, “I’m the creeper: catch me if you can.”
As the internet became more widespread, many people didn’t understand the risks of having connected data and computers with little cyber protection. It was not a significant concern since few malicious programs existed.
When did this begin to change?
In 1989, Joseph Popp created one of the first malicious computer attacks. He made a malware program called the “AIDS Trojan.”
Initially passed by a floppy disk, the program was poorly designed and did not disable the computer. The main thing it did was scramble the names of the files.
Thankfully, programmers combated the virus quickly with the proper computer software.
Later in 1989, a second cyberattack started circulating, but this one was not programmed to be malicious.
Instead, the creator wanted to raise awareness.
Robert Morris was concerned about how much data was easily accessible on the internet. He saw how much of the data was poorly protected by inadequate security and weak (or nonexistent) passwords.
To show people how vulnerable the current security was, Morris developed a computer worm that significantly slowed down the internet.
While the worm was programmed to prove a point and do no actual damage, estimates say it cost between $100,000 and $10,000,000 from lost productivity, unstable internet, and restarting IT systems.
Whether Morris expected this kind of damage or not, his point was made – even before the internet was widely available, cyberattacks were both real and dangerous.

Cybersecurity Today
In today’s world, cybersecurity is a part of life.
With virtually everything connected online, cybersecurity has never been more critical.
Sadly, it is still common to hear stories of data breaches.
It is not uncommon to read stories of banks, credit card companies, online retailers, phone companies, and other companies having their systems breached and customer’s data stolen.
Thankfully, there are many companies actively developing better cybersecurity programs. Microsoft, Apple, and Google are constantly updating the software used on computers, servers, tablets, phones, and other devices.
Governments are also recognizing the investment they need to make to protect their servers and classified data.
In 2019, the U.S. government expected to pay around $15 billion to protect its data. The Department of Defense and Homeland Security use up the majority of this budget.
Do You Need Outsourced IT Services So You Can Focus On What Matters?
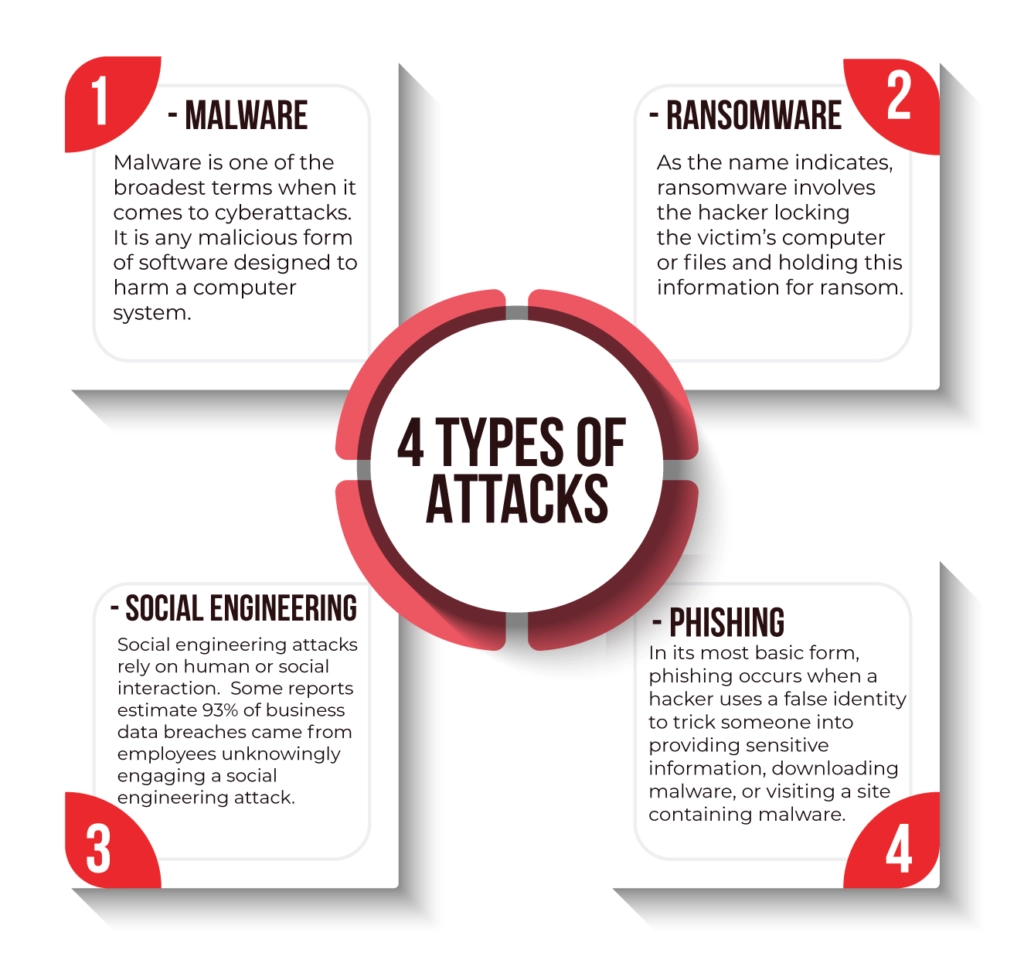
So, what are some of the most common cyberattacks? While many exist, let’s look at four of the most common attacks.
Malware

Malware is one of the broadest terms when it comes to cyberattacks. It is any malicious form of software designed to harm a computer system.
When malware enters a computer, it performs a malicious function such as stealing, deleting, or encrypting data, monitoring a computer users’ activity or hijacks core computing functions.
Common malware includes worms, viruses, Trojan horses, and spyware.
Malware is designed to steal, encrypt, or delete data, alter or hijack core computer functions, or track a computer user’s activity without their knowledge.
Malware is commonly distributed through physical hard drives, USB external drives, or internet downloads.
Ransomware
As the name indicates, ransomware involves a hacker locking the victim’s computer or files and holding this information for ransom. It typically requires the victim to produce a payment before the hijacked files and system are unlocked.
Ransomware spreads through phishing emails or unknowingly visiting an infected website.
Ransomware is devastating due to the difficulty in recovering affected data.
While some victims do choose to pay the ransom, there is no guarantee the hacker will give control of the computer or files back to the victim.
For an example of ransomware to watch out for, read our related blog post about Ryuk Ransomware.

Do You Need Outsourced IT Services So You Can Focus On What Matters?
Social Engineering Attacks
Social engineering attacks rely on human or social interaction, not just bots entering a computer through the internet.
And because humans are prone to error, social engineering is the biggest security risk today.
How much of a risk?
Some reports estimate 93% of business data breaches come from employees unknowingly engaging with a social engineering attack!
Social engineering attacks occur when a hacker tricks someone to give them information or access to software or data. Hackers try to manipulate people into breaking standard security procedures.
What makes social engineering attacks so effective?
Because it relies on human interaction, social engineering attacks usually play on a person’s emotions.
One of the most common tactics is to have someone think they are helping someone in need. For example, an attacker may pose as a fellow employee or a family member asking for access to a document, bank account, or sensitive data.
Think about it—a properly built IT system can prevent a malware attack, but it cannot stop an employee from giving a password to a hacker posing as a coworker.

So how do companies combat social engineering attacks?
Many companies have regular training for employees on how to spot social engineering attacks and strategies.
It is also essential for businesses to have guidelines in place when working with sensitive data.
For example, a common rule is not allowing employees to share company usernames or passwords electronically. If an employee forgets a password, they should call a coworker instead of emailing them.
Phishing
Phishing is a type of social engineering attack that has become one of today’s most common and malevolent cybersecurity attacks.
Phishing occurs when a hacker uses a false identity to trick someone into providing sensitive information, downloading malware, or visiting a site containing malware.
What makes phishing so prevalent?
The extensive use of electronic communication, including email, text messaging, instant messaging, and social media accounts, makes phishing an extremely prolific type of attack.

What are some common phishing scams?
One of the most common phishing attacks targets people through email. An attacker creates an email looking like it comes from your local bank or the government, and the email asks you to visit a website and enter your username and password.
Another common tactic is creating a fake social media account resembling a friend or family member. The hacker then asks for money or data through messaging, and it appears it is your family member or friend asking for a favor.
What can be done to protect from phishing?
Like other social engineering attacks, having training and guidelines in place is a crucial first step to protecting yourself from phishing.
Employees should be trained to look for specific phishing patterns and tactics. As a business owner, you should make sure your employees know several tell-tale signs of phishing.
What are some common signs of phishing attacks?
- Generic language such as “Sir” or “Madam”
- Incorrect grammar, language, or punctuation
- An odd sense of urgency
- Unusual requests for sensitive information
For example, emails from fake IRS accounts asking for personal information are a common phishing tactic. However, the IRS (and most businesses in general) makes it clear that they communicate through postal mail and NOT through email.
If you or an employee receives a sensitive request from a business or a direct message from a social media friend, contact the company or person directly to see if the request is legitimate.

Do You Need Outsourced IT Services So You Can Focus On What Matters?
8 Top Cybersecurity Threats [& How To Protect Your Business]
With the background we have on what a cyberattack is and several common attacks, let’s focus on what this means for a small business.
As a small business owner or employee, you know how important your security and data are. Even if you have a dedicated IT service provider, it is still good to know the technology threats your business faces.
Straight Edge Technology provides IT services and network security in the San Antonio and Corpus Christi areas. As a private business ourselves, we know and understand how important your security is to you and your company.
The following are some of the top cybersecurity threats Straight Edge Technology sees for small and mid-sized businesses in 2022.
In each section, we also include several practical guidelines your company can implement to reduce your risk and exposure to these attacks.
These cybersecurity threats and their preventions are available to download in PDF format at the end of this article.
Some of these threats and their solutions are basic, and others are complex.
Working with a managed IT service company helps protect your business from these threats. Even if your company has an IT department, we recommend consulting an outside IT company to ensure you have maximum security.
Are you ready to be more confident about your company’s cybersecurity entering 2022?
Let’s get started!
Threat 1: Phishing
As mentioned before, phishing is one of the most common cyberattacks due to the high levels of interaction humans have on electronic communication.
Straight Edge Technology sees this becoming even more of a threat as email and instant messaging increase in the business world.
Why does a rise in electronic communication increase the threat of phishing?
Office employees receive hundreds of emails and electronic messages every day. Towards the end of the workday, as we get tired, we become susceptible to making bad decisions.

Attackers know this, and some choose this time of day to bombard employees with fake emails and social media accounts. After all, a hacker only needs one employee to make a mistake to destroy a business’s integrity.
Sadly, this happened in 2019 to the Carle Foundation Hospital.
Through a phishing scam, hackers gained access to three of the employee’s email accounts. The ensuing investigation determined these accounts gave the hackers access to sensitive patient medical records and Social Security information.
Thankfully, the hospital did the right thing and contacted all affected patients. It also recognized the need for more employee training on how to spot phishing scams.
What should your company do to protect itself from phishing?
First, watch for unusual emails and instant messages. They may start with unusual wording such as “Dear Customer” instead of using your name, have bad grammar, or have a generic signature.
Second, be cautious in clicking links or giving sensitive information, even if it appears legitimate. If in doubt, directly contact the source to make sure they sent the message.
And third, install anti-phishing toolbars on internet browsers. These toolbars alert you to sites containing phishing information.
Threat 2: SMS-Based Phishing (Smishing)
At first glance, it may appear SMS-based phishing (also called “Smishing”) falls under the general “phishing” category, but there are several key differences.
While general phishing often occurs online through emails or web browsing, smishing occurs through SMS text messages on your phone.
How does it work?
The attacker sends an SMS text message to a user’s phone. Opening the text message itself doesn’t start the attack, but the message contains a link. If the link is clicked, it begins the attack.

Why are more attackers turning to SMS-based phishing over traditional email phishing?
Many email programs, such as Google or Microsoft Outlook, are smart enough to detect phishing emails and label them as spam. This means the average email user doesn’t even notice most phishing attacks.
However, anyone can still get a text message and open a bad link!
What are common smishing attacks?
- A message from “your bank” asking you to enter your social security number.
- A “delivery carrier” asking you to schedule a package delivery.
- Other organizations asking you to click a link or give information.
What should your company do to protect itself from SMS-based phishing?
First, never open a link in a text message. Most banks and businesses do not ask for information via SMS message – they call or mail you.
Second, watch for misspellings or generic language. Like email phishing, smishing often contains generic language like “Dear Customer, “Sir,” or “Madam.”
And third, if you think the message is legitimate, call the business directly or go to your online account to give the information. This ensures no valuable data falls into the wrong hands.
Threat 3: PDF Scams
Similar to phishing, PDF scams have one goal in mind: To get you to open an attached PDF.
They involve an email being sent with a message, often stating a security policy has been updated or an account statement is attached.
When you click the attached PDF, however, it exposes you to malware or ransomware on your computer.
What makes PDF scams effective?
Unlike many email scams, PDF scams often don’t ask you to open a link to give information.
PDF scammers know people are wary of an email asking them to click a link. However, people are more likely to open a PDF if they think it is a statement balance or press release.

What makes PDF scams especially viable in the workplace?
In the office, PDF attachments are constantly shared through email, Slack, and other messaging platforms. Our brains associate PDFs with business, and therefore we are more likely to let down our guard and open them.
What should your company do to protect itself from PDF scams?
First, train your employees to watch for generic or unusual email addresses. For example, if someone gets bank statements through email, ensure the sender’s email address is from the bank and not a generic address.
Second, watch for unusual and generic headings. Instead of using your name, PDF scams often use generic terms like “Sir” or “Madam.”
And third, make sure you have updated and secure virus protection on your computers and network. If someone happens to open up a PDF scam, having security in place goes a long way in protecting your business and alerting your IT department.
Do You Need Outsourced IT Services So You Can Focus On What Matters?
Threat 4: Malware & Ransomware
We already discussed the devastating impact malware and ransomware have when they infect a computer system. This results in many possible problems, including:
- Lost data
- Frozen systems
- Hijacked software
Although not based on social interactions, Straight Edge Technology still views these attacks as highly prevalent in 2022, especially in small businesses.
Why do we think non-phishing attacks are here to stay?
Hackers know every business keeps its data on servers connected to the internet. All they need is one crack in your security, and they can perform the attack.
Sadly, Pitney Bowes Inc. experienced this first hand.
Pitney Bowes Inc. helps small businesses with e-commerce, shipping logistics, and mailing services.
In early 2019, they became victims of a malware attack that encrypted information on some of their systems and affected customer’s ability to access the company’s services.
Although there was no evidence that customer records had been stolen, the malware crippled the company’s servers. Customers were not able to upload transactions, access their accounts, or refill their postage.
When they realized they had been attacked, Pitney Bowes Inc. immediately had their technical team assess and fix the situation. They also brought in 3rd-party IT consultants to prevent future attacks.
What should your company do to protect itself from malware and ransomware?
First, make sure you keep all your computer software and hardware updated. Outdated software, drivers, and other plugins are common security vulnerabilities. If you have an IT service provider, check with them to make sure this is happening on your servers.
Second, enable click-to-play plugins to keep Flash or Java from running unless you click a link. This reduces the risk of running malware programs with Flash or Java.
And third, removing old software, sometimes referred to as Legacy Apps, reduces risk. For example, if your computer has Windows 10, but you run programs designed for Windows 7, these are considered Legacy Apps and may be a security risk. Your software company should be able to give you an updated program designed for Windows 10.
Threat 5: Database Exposure
Database exposure is what it sounds like: A security breach exposes database information to hacking or theft.
Database exposure occurs in a variety of ways.
Some hackers use social engineering attacks to steal login credentials, and others use malware to gain access.
Because most companies use servers to host customer information, Straight Edge Technology sees database exposure being a big concern in 2022. Most company databases include customer contact information, financial records, or identity records such as Social Security numbers.
One of the significant issues with database exposure is the fuel it becomes for social engineering attacks.

For example, let’s assume a company has a database exposure that releases names, email addresses, and birthdates.
Using this information, a hacker could fake a local hospital’s identity and send each person an email with their name and birthdate. These people are more likely to open a link in the email because it includes personal information (their name and birthdate), and therefore appears to be legitimate.
Recently, around 250,000 American and British job seekers had personal information exposed when two recruitment sites, Authentic Jobs and Sonic Jobs, failed to set their cloud databases as private.
As a result, personal information, including phone numbers, email addresses, driver licenses, and salary expectations, were made public.
After learning about the exposure, the two companies immediately made their databases private.
It is unknown how much of this information was harvested by hackers, but it provided a gold mine of personal data for potential social engineering cyberattacks.
What should your company do to protect itself from database exposure?
First, if you have a private server, keep the physical hardware in a secure and locked room. This helps prevent theft if your building is robbed, and it keeps unauthorized personnel from accessing it with a portable hard drive.
Second, make sure you have a database firewall and web application firewall. A locked door protects your physical server and hardware, and firewalls protect your server on the internet.
Third, keep access to the server limited. Each person with a login to the server is a potential leak, so the fewer logins, the better.
And fourth, encrypt the data on the server and keep a regular backup.
Threat 6: Credential Stuffing
Credential stuffing is an attack geared toward stealing user access through login credentials. This is most common in situations where the same login credentials are used for multiple sites or accounts.
With most programs being online, Straight Edge Technology expects credential stuffing to be a significant threat in 2022.
Canada Post, the postal operator in Canada, recently discovered some of their users’ account information had been hacked in 2017 by credential stuffing.
Although the exact number of affected accounts was unknown, Canada Post immediately began resetting all their user’s passwords.

While investigating the incident, it became clear Canada Post was not to blame.
Instead, most of the accounts were accessed because customers used the same login credentials across multiple sites, with Canada Post being one of them.
As a result, if a user’s account was hacked on another website and the user had the same login credentials on Canada Post, the hackers could access the Canada Post account as well.
What should your company do to protect itself from credential stuffing?
First, implement 2-Factor Authentication for account logins. This requires an email or phone verification along with the standard username and password.
Second, use different passwords for every account and program your employee’s access. If one account is hacked, the hacker will not have access to more accounts with the same password.
And third, never share passwords with other people. If you have a shared account for some reason, always give the password verbally, never through electronic communication.
Do You Need Outsourced IT Services So You Can Focus On What Matters?
Threat 7: Accidental Sharing
We’ve all seen it happen, and maybe it’s happened to you: The dreaded “Reply All” to an email when you only meant to reply to one or two people.
Suddenly, everyone in the office knows your true feelings about the manager or boss!
Accidental sharing is a similar problem. It occurs when information is shared or leaked accidentally. It is usually the result of human error, not because of malware or a hacker.
Accidental sharing includes personal or business data, and it is shared through emails, unsecured forms, messaging or social media platforms, and a host of other ways.
Accidental sharing includes personal or business data, and it is shared through emails, unsecured forms, messaging or social media platforms, and a host of other ways.

Because accidental sharing is based on human error, Straight Edge Technology sees it being a problem in 2022 and for many years to come. It is a particular threat to companies where large numbers of employees have access to primary databases.
EA Games had an accidental sharing incident during their FIFA 20 Global Series online competition.
When players registered for the event, they entered their sign-up information on a form on EA Games’ website. However, when new players went online to register, the registration form was pre-filled with personal information of players who had already signed up for the competition.
Obviously, the players were upset with their information being displayed. It was especially upsetting because it didn’t appear EA Games was hacked. The issue was an accidental sharing issue inside EA Games, not the result of a cyberattack.
When EA Games became aware of the issue, they shut down the registration for several days until their IT team fixed the problem.
What should your company do to protect itself from accidental sharing?
First, limit the number of employees who have access to data. The more people who have access to information, the higher the chance for human error in sharing the data.
And second, implement user activity monitoring software. This allows you to track and discover if your data is in danger. It also provides solutions to prevent accidental sharing.
Threat 8: Man In The Middle Attack (MITM)
Do you remember playing “monkey in the middle” or “keep away” when you were a child? In these games, several children throw a ball back and forth, and one or two other children stand in the middle trying to intercept the ball.
The Man-In-The-Middle (MITM) security attack works in the same way. A hacker gains access to a line of communication and takes control of the communication by playing in the middle.
Also referred to as a “machine in the middle” or “monster in the middle,” attack, this attack works on a fairly basic principle:
- An attacker gains access to a line of communication. Some of the most common hacks occur through IP, DNS, or HHPS spoofing. Email hijacking or WiFi eavesdropping is also frequently used.
- When Person A sends information to Person B, the attacker is in the middle and intercepts the information. The attacker can then modify, steal, or use the information.
- Example: If Person A sends a message that says, “My password is acme1234,” the hacker in the middle immediately has the password. Then, the hacker can tell Person B “My password is apple5678.”
- Or, the hacker can allow the original message to go through and simply steal the information.
- Because it appears to come from Person A, Person B will think it is a legitimate message.
The security concerns are obvious: If someone thinks they are talking to a person, website, or online program through a secure connection, then they are much more likely to provide passwords, bank information, client data, social security numbers, and much more.
In 2019, MITM hackers stole a $1 million wire transfer between a Chinese venture-capital firm and an emerging Israeli startup. Using elaborate domains and email systems, the hackers were able to make the capital firm and startup think they were talking to each other, but in reality, they were communicating through the man-in-the-middle hacker network.

What should your company do to protect itself from main-in-the-middle cyberattacks?
First, avoid WiFi connections that are not secure. If you have employees working remotely, don’t allow them to access sensitive company data over public WiFi networks.
Second, make sure your employees do not interact with websites that are not secure. If a URL is not a secure website, it will only show “HTTP” instead of “HTTPS” in front of the URL. The browser should also show an alert that the URL is not secure. If this happens, leave the site immediately.
And third, make sure that your internet connections and internet devices are always updated with the latest security updates. Having outdated software or unsecured internet portals creates potential access points for MITM hackers.
Conclusion
In a world where the internet connects everything, cybersecurity has never been more critical.
While having IT services and updated software and hardware is important, it is still critical to understand that today’s hackers target human behavior through social engineering hacks.
Thankfully there is training, software, and help available for individuals and small businesses!
Straight Edge Technology highly recommends you partner with an IT service provider if you are a small business. Even if you have your own IT department, it is good to receive coaching and another set of eyes on your company’s security.
We offer support for a variety of industries including:
- Healthcare IT services
- Legal IT support
- Oil & Gas IT services
- Manufacturing IT services
- Construction IT support
If your business is looking for IT services in San Antonio, TX, Corpus Christi, or the surrounding cities in Texas, then contact our team at Straight Edge Technology today.
We would love to talk with you, discuss your company’s goals, and plan how your IT can work for you in growing your business!
Do You Need Outsourced IT Services So You Can Focus On What Matters?
Read our recent blog posts on different IT services, challenges, and tips!

7 Ways Law Firms Can Benefit From 24/7 IT Monitoring
In the fast-paced world of law, where every second counts and sensitive client data must be protected at all costs, technology plays a pivotal role

Lunch and Learn: Hurricane Preparedness Form & Checklist
Straight Edge Technology recently hosted a Lunch and Learn where we explored crucial topics related to Hurricane Preparedness and Disaster Recovery. In our ongoing effort

Managed IT Services: A Key Partner In Healthcare Disaster Recovery Plans
In today’s digital landscape, healthcare organizations face a unique set of challenges in maintaining the security and accessibility of their data. From patient records to

